The internet you know — Google, YouTube, X, Reddit — is only part of the story. Beyond the familiar web lies a world of encrypted tunnels designed to protect privacy, resist censorship, and hide digital footprints.
One of the least-understood of these networks is I2P, or the Invisible Internet Project — a powerful tool for anonymity that rivals Tor, yet works differently.
Story Synopsis
I2P is an open-source, decentralized privacy network that allows users to browse, host websites, and exchange data without revealing their real IP addresses. It was first developed in the early 2000s and remains one of the most advanced technologies for anonymous communication.
Unlike traditional browsers that rely on direct internet routing, I2P builds a private layer within the internet — a self-contained ecosystem where users connect through encrypted tunnels called “I2P routers.” These tunnels make it nearly impossible to trace who’s communicating with whom.
What It Means
In simple terms, I2P is the “internet within the internet.” While Tor focuses on anonymous access to the public web (the “surface web”), I2P creates its own enclosed network, known as the “I2P network” or “I2Pnet.”
Within I2Pnet, websites are called “eepsites” — domains ending in .i2p that are only accessible through the I2P software. You can:
- Host private forums, file shares, and blogs without public exposure.
- Send encrypted messages and emails.
- Access hidden services that don’t exist on the regular web.
It’s privacy-focused, but not inherently “criminal” — researchers, journalists, and activists often use I2P to bypass surveillance and protect sources.
How It Works
1. Layered Encryption
Every connection through I2P is routed via multiple encrypted tunnels — inbound and outbound. Each tunnel uses one-way encryption, meaning no single relay knows both the sender and the receiver.
2. Garlic Routing
Instead of Tor’s “onion routing,” I2P uses “garlic routing,” bundling multiple messages together (like cloves in a garlic bulb). This adds an extra layer of confusion for anyone trying to analyze network traffic.
3. I2P Router Software
To join the network, users install the I2P Router, available for Windows, macOS, Linux, and Android. Once running, it connects your device to a mesh of other routers, forming a decentralized web of peers.
4. Accessing Eepsites
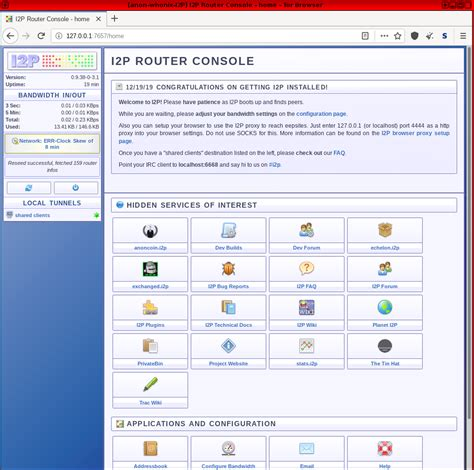
After installing I2P, you can visit .i2p sites using the built-in proxy interface (usually at http://127.0.0.1:7657). Popular eepsites include privacy wikis, community forums, and file repositories — all invisible to Google or Bing.
Why It Matters
Freedom of Information
In regions where censorship blocks news or social media, I2P offers a backdoor to free expression. It allows users to communicate and publish without revealing identity or location.
Beyond Tor
While Tor connects users to the “dark web,” I2P focuses on building a self-contained private network, making it better for peer-to-peer services, messaging, and hosting content securely.
Security vs. Legality
Like any anonymity tool, I2P can be used for both good and bad. Law enforcement agencies monitor such networks for illegal activities, but using I2P itself is legal in most countries — as long as you’re not engaging in unlawful behavior.
A Living Example of Decentralization
I2P has no central server. Each user contributes bandwidth and routing capacity, embodying the original decentralized spirit of the internet.
How to Use I2P (Step by Step)
- Download the I2P Router
Visit geti2p.net and download the appropriate installer for your operating system. - Install and Launch
After installation, open the I2P router console (it runs locally in your web browser athttp://127.0.0.1:7657). - Wait for Connections
The router will automatically connect to peers. This may take several minutes as it builds encrypted tunnels. - Access Eepsites
Use the “I2P Browser” or configure your regular browser’s proxy settings to127.0.0.1:4444. Then explore.i2pdomains such ashttp://identiguy.i2porhttp://stats.i2p. - Host Your Own Services
The console allows you to create private websites or file shares — perfect for secure collaboration or hidden communities. - Optional: Use I2P for Torrents or Messaging
I2P supports privacy-focused torrenting and encrypted messaging via integrated apps like I2PSnark (for files) and I2P-Bote (for email).
Tech Tidbits
- I2P’s “garlic routing” was one of the first methods to mix messages for anti-correlation analysis — more complex than Tor’s circuit model.
- There are over 100,000 active routers on I2P at any given time.
- I2P can run inside Tor for “double anonymization,” though it’s slower.
- Because of peer-to-peer routing, I2P can work even during partial internet shutdowns.
- Developers are working on I2P Browser, a Firefox-based launcher similar to the Tor Browser for easier use.
Suggested Reading
- “The Invisible Internet Project (I2P): Official Documentation” — I2P Project
- “Tor vs I2P: What’s the Difference?” — Restore Privacy
- “How Anonymous Networks Work: Tor, I2P, Freenet Explained” — MakeUseOf
- “How I2P Helps You Bypass Censorship and Stay Private Online” — PrivacyGuides