Every time you log into a website, you leave behind a digital trail that cybercriminals may one day exploit.
Behind the scenes of the internet’s dark corners lies a booming marketplace — one where stolen credentials are bought, sold, and repurposed like consumer goods. These black-market economies turn your logins into currency, fueling everything from identity theft to ransomware.
After examining several dark web markets and leaked data sets, this is how the underground trade in digital identities really works.
From Breach to Sale: The Lifecycle of a Stolen Credential
The journey of a stolen credential usually begins with a breach, phishing scam, or infostealer malware infection. Once compromised, these details are sorted, repackaged, and distributed through an intricate chain of brokers and marketplaces.
Attackers use a variety of techniques to acquire credentials:
- Phishing emails trick users into surrendering login information directly.
- Infostealer malware quietly extracts saved passwords, session cookies, and browser data.
- Data breaches expose entire company databases, which are later resold in bulk.
- Credential stuffing automates the testing of leaked username-password pairs across multiple services.
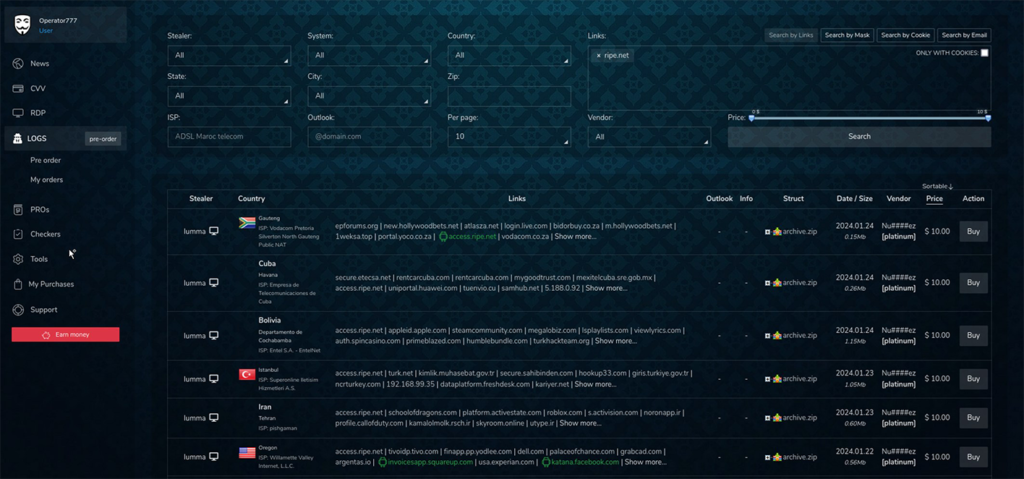
Once data is harvested, it’s uploaded to darknet markets, where cybercriminals operate in anonymity using cryptocurrency. Many sellers specialize in “combo lists” — massive text files combining usernames and passwords from multiple leaks — while others offer curated, high-value access to specific organizations.
According to threat analysts, listings can range from $10 for common accounts to several thousand dollars for corporate network access. Some vendors act as initial access brokers, offering remote entry points to business systems later used by ransomware groups.
The Hidden Marketplace: How the Dark Web Trades Your Data
Contrary to the idea of a single “dark web,” this illicit economy spans dozens of encrypted forums, Telegram channels, and darknet marketplaces accessible only through Tor or similar privacy tools.
Each marketplace functions like a miniature e-commerce site — with:
- Seller profiles and reputation scores
- Escrow services to ensure both buyer and seller security
- Forums for feedback, tips, and trade discussions
- “Access-as-a-Service” listings for pre-compromised networks
The sophistication mirrors legitimate platforms: verified vendors, customer support, even refund guarantees if stolen credentials don’t work.
A research study of one such market revealed that over 1,000 user profiles were sold within five months, generating up to $4,000 in daily revenue. High-demand listings often target financial institutions, enterprise VPNs, or government portals.
Why It Matters
The scale of this underground trade goes far beyond simple account theft. It fuels an entire cybercrime supply chain:
- Credential Reuse Attacks – Stolen logins are tested across multiple services using bots, exploiting users who reuse passwords.
- Corporate Intrusion – Once inside a company system, attackers can escalate privileges, deploy malware, or exfiltrate sensitive data.
- Identity Theft & Fraud – Bank, email, and e-commerce logins can be used to impersonate victims or launder funds.
- Ransomware Deployment – Criminals purchase network access from brokers, then launch large-scale attacks.
- Reputation Damage – When stolen accounts are used for scams, the original owner may face legal or financial consequences.
Every reused password becomes a potential gateway to another breach. The commoditization of credentials turns individual mistakes into collective risk.
The Economics of the Underground
Just like any black market, the value of stolen data depends on freshness, exclusivity, and utility.
- Email and social accounts fetch between $1 and $30 each.
- Corporate VPN access can exceed $500.
- Cloud service credentials for platforms like AWS or Azure may sell for thousands.
Data sets are frequently repackaged — meaning the same credentials may appear on multiple markets.
Advanced actors often combine stolen data with AI-based profiling to identify valuable targets, filtering users with corporate ties, cryptocurrency wallets, or financial accounts.
In short: stolen credentials aren’t just leaked — they’re refined, rated, and recycled for profit.
How to Protect Yourself and Your Organization
Defending against this growing underground industry requires both individual vigilance and enterprise strategy.
For individuals:
- Use unique passwords for every account.
- Rely on a password manager to generate and store complex credentials.
- Enable multi-factor authentication (MFA) on all major accounts.
- Be cautious of phishing emails or suspicious login requests.
For organizations:
- Enforce MFA and password rotation policies.
- Deploy dark web monitoring tools to detect leaked employee credentials.
- Segment networks to limit lateral movement after a compromise.
- Conduct regular security awareness training to prevent social engineering.
- Use behavioral analytics to identify unusual login patterns or credential abuse.
Tech Tidbits
- Over 11.7 billion credentials have been leaked globally since 2020.
- Around 61% of breaches involve compromised passwords.
- Infostealer malware is now offered as a subscription service, lowering the barrier for entry.
- Dark web marketplaces earn millions annually from “access-as-a-service” models.
- Commonly used credentials like “123456” or “password” remain alarmingly prevalent, even in 2025.
Publication / Release Details
Feature: Analysis of dark web credential markets and their global impact
Research period: September–October 2025
Primary focus: Illicit sale of credentials, malware-based theft, underground trading structures
Availability: Ongoing research based on live threat intelligence and public domain sources
Suggested Reading
- “The Hidden Economy of Credentials on the Darknet” – DarkOwl
- “Sale of Stolen Credentials and Initial Access Dominate Dark Web Markets” – Dark Reading
- “Leaked Credentials Leads Are Candy for Dark Web Actors” – Recorded Future
- “Understanding Infostealer Malware and Its Role in Credential Theft” – Help Net Security